An Interactive Universe Awaits
Welcome to Quenq, a living museum of digital history. We build unforgettable web experiences that bring back the magic of the early internet. Dive into our flagship Windows XP simulator, lose yourself in a massive arcade of classic Flash games, or leave your mark on a collaborative pixel art canvas.
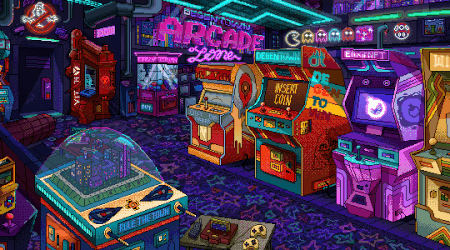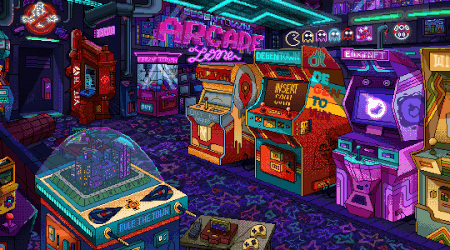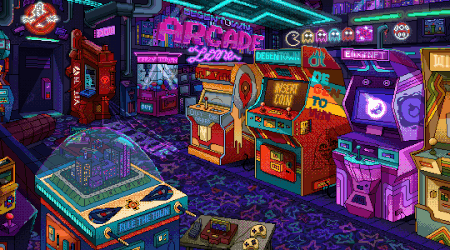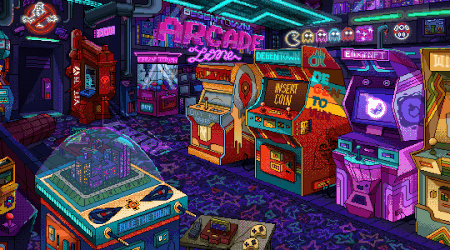
Rediscover the golden age of browser gaming. The Quenq Arcade is a meticulously curated library of the best emulated Flash games. From legendary titles to hidden gems, we're preserving the legacy of browser-based fun with a focus on quality, performance, and pure nostalgia.
The Labs are our digital playground for bleeding-edge web experiments. This is the home of our flagship Reborn XP simulator, along with a growing collection of powerful tools, classic system emulators, and unique interactive toys. See what's possible when passion for detail meets the power of the browser.
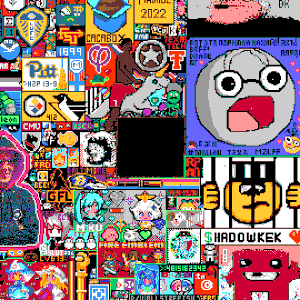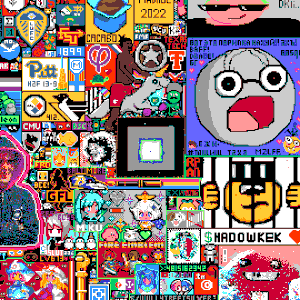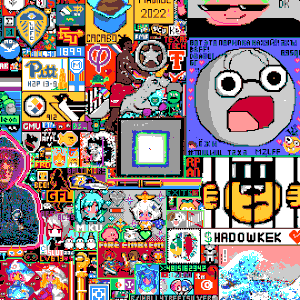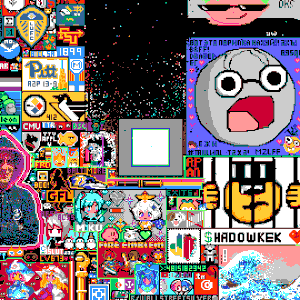
Join a living social experiment in collaborative art. Inspired by Reddit's legendary `r/place`, our canvas is a massive, real-time pixel battleground. With a faster cooldown, and a live chat, you can work alone or with a community to create art, wage pixel wars, and leave a temporary, beautiful mark on internet history.
